Solving the darknet riddle
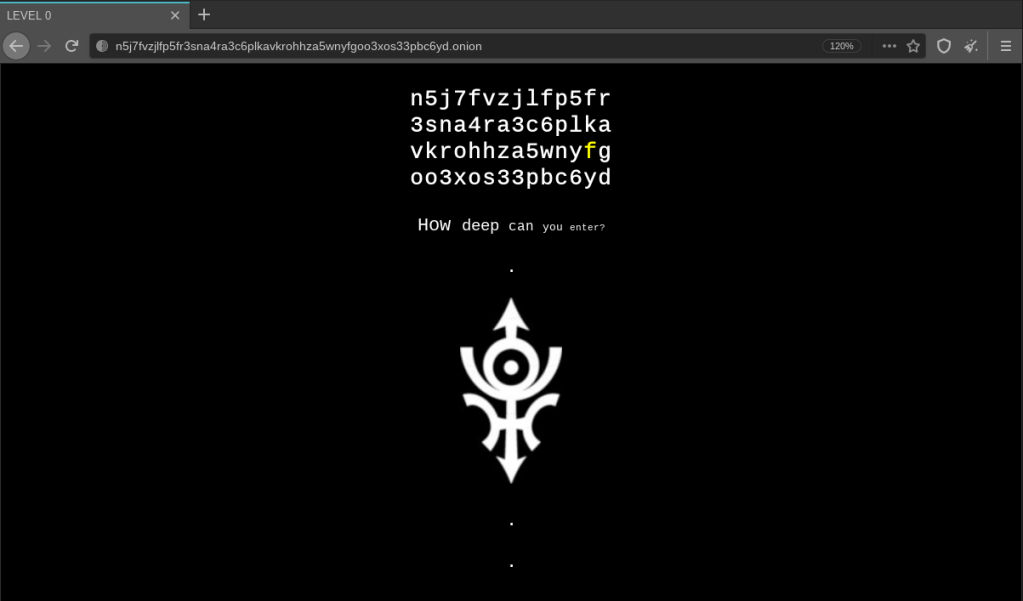
An ‘.onion’ link was posted on Reddit back in June 2020 with a suspected riddle. It got me curious.
Some random characters and a sentence: “How deep can you enter?”
Within the page source-code a comment was present with a series of numbers/letters that looked like a hexadecimal.
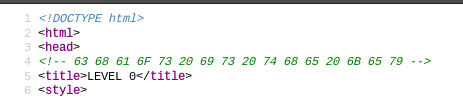
After converting the hex to ASCII it read: ‘chaos is the key’.
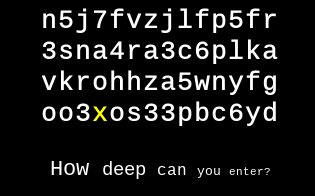
I noticed that when the page is refreshed, every time a different letter is highlighted in yellow.
When the ‘x’ char was highlighted a link was appended to the word ‘enter’…
The link was to an image (below).

After google translating the text in the image which did not reveal anything useful, it was time to examine the image file itself.
I suspected the next “message” would be hidden in image metadata or perhaps a pixel analysis would need to be done but after downloading the file and opening it, the message was already visible.
See the image area below, it may not be visible in the browser but if you download it and look closely enough you’ll see it.
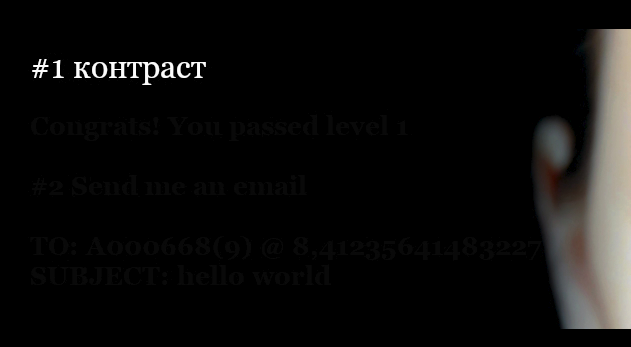
The hidden message contained another riddle: Congrats! You passed level 1 #2 Send an email TO: A000668(9)@8,41235641483227 SUBJECT: hello world
The domain part of the email was easier to figure out, after a quick google it was apparent that it’s ‘protonmail.com’.
The first part of the email turned out to be a the 9th Mersenne prime number. Making the email address [email protected].
Few hours after sending the email I received a response with a binary code in the message.
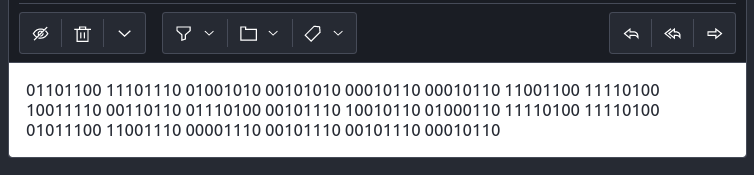
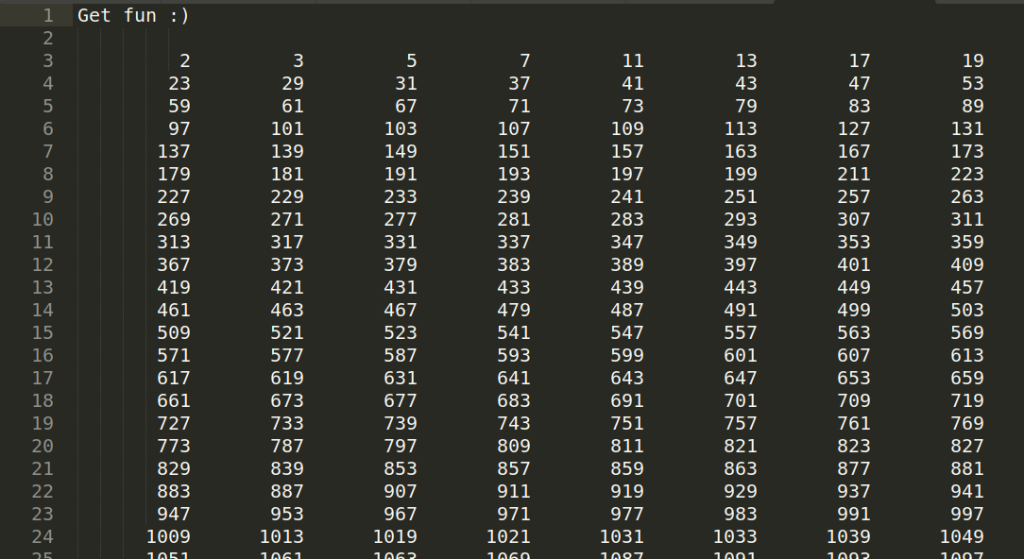
Binary conversion revealed an URL that contained a text file called ‘haystack.txt’.
There was also an instruction in another file that stated:
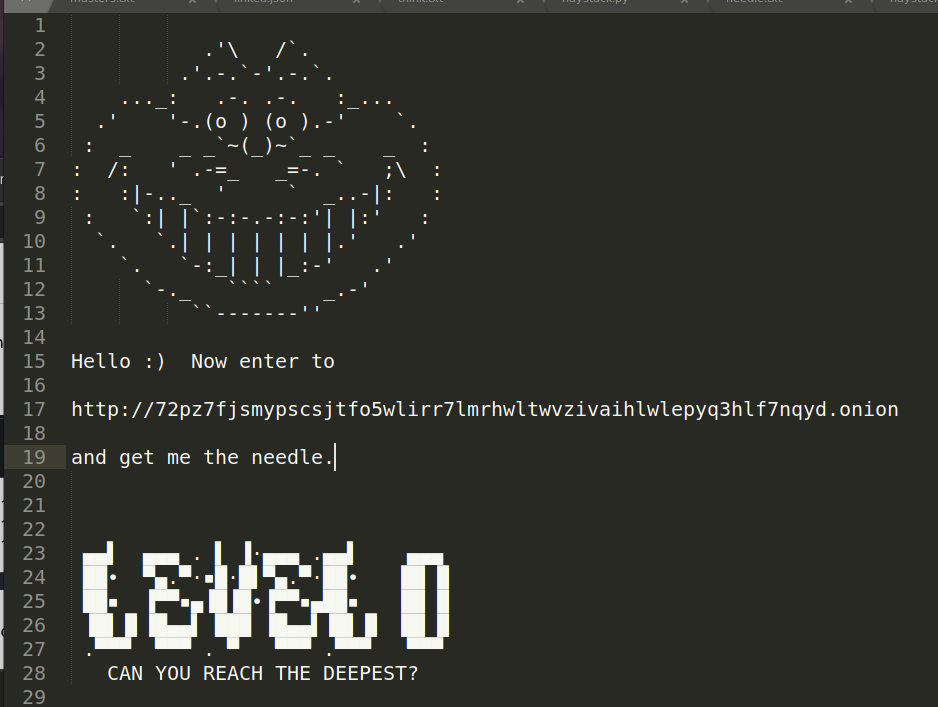
At this point it was apparent that there is a ‘needle in a haystack’ file.
The numbers in the text file appeared to be prime numbers and my next thought was to check if there are any non-primes in the file.
There was 1000000 numbers in the file. Manually checking each one was out of the question so I turned for help to Python. I wrote a quick script to check for primes, output non-prime numbers (if any) and left it running.
After a while one non-prime number was returned.
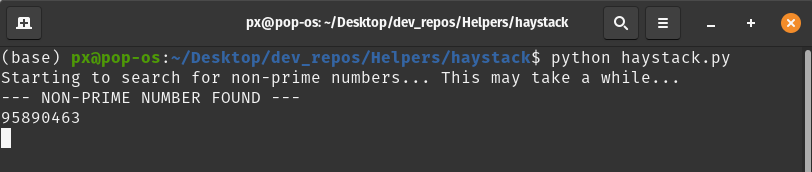
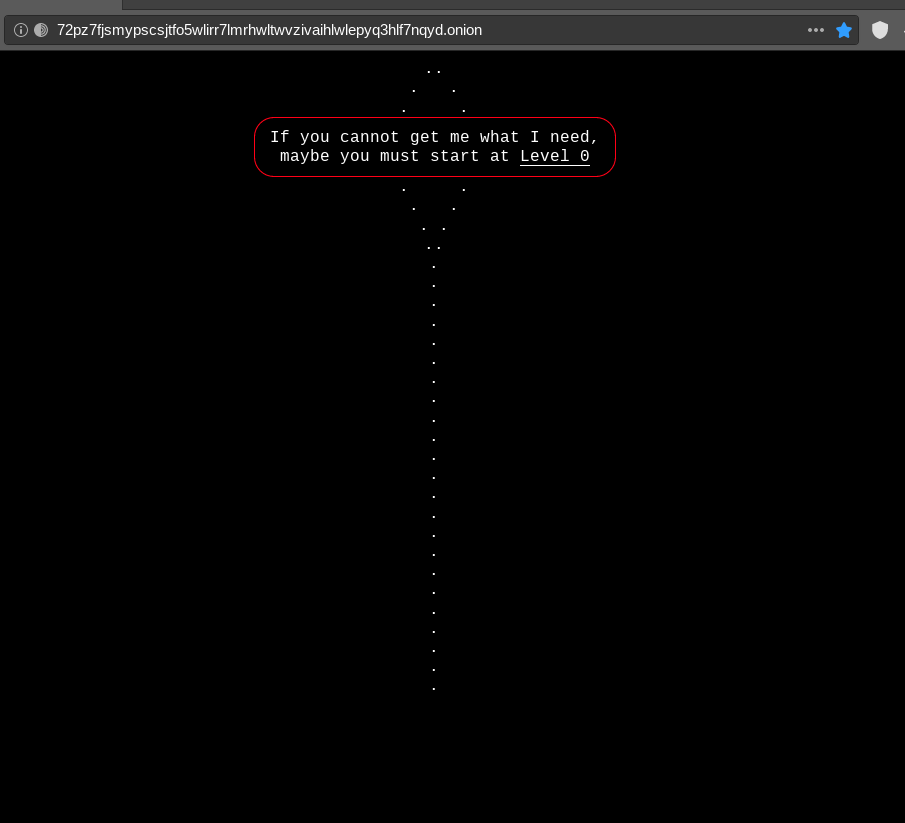
Next part of the puzzle was to navigate to the provided URL and use the needle somehow. The URL contained a a short message:
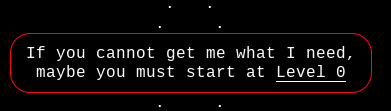
‘If you can not get me what I need, maybe you must start at Level 0‘
There was no inputs or buttons on the page but there was some clues left. It took me a short while to figure it out. The clues were hidden in the following parts of the puzzle:
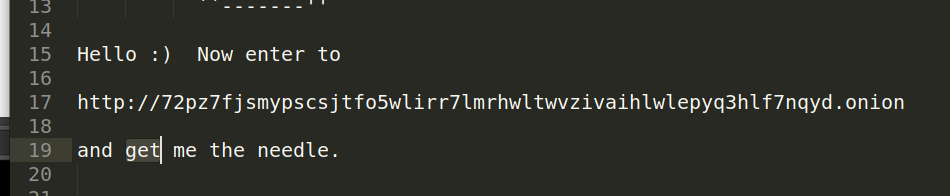
Clue 1:
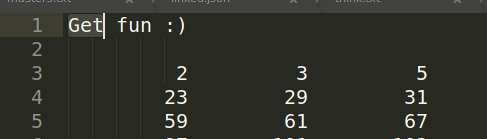
Clue 2:
Clue 3:
The ‘get‘ word was chosen purposely and it referred to a http GET request.
After making the GET request while passing the non-prime ‘needle’ as the parameter another message appeared.
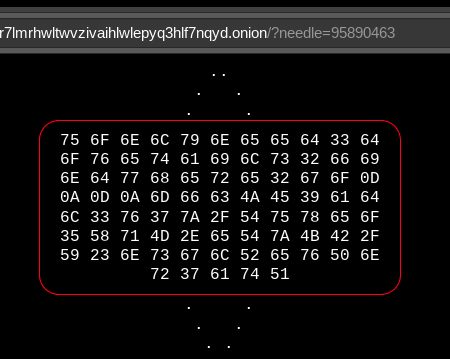
The message was in hexadecimal and after converting it, another puzzle was revealed:
uonlyneed3dovetails2findwhere2go mfcJE9adl3v7z/Tuxeo5XqM.eTzKB/Y#nsglRevPnr7atQ
‘You only need 3 dovetails 2 find where 2 go’

This took me a while to figure out. At first I though it may have something to do with the ‘ / ‘ but after a quick research I realized that dovetail is also a thing in card games and it’s a riffle-shuffle technique.
This would mean that the provided string needs to be riffle-shuffled 3 times to reveal where to go.
I seem to have lost the python script I wrote back then to do this for me but after it has done shuffling, the string has formed another URL.
After entering the URL, it seemed like it was the last puzzle (at least until more parts are developed):
That was FUN!
To whoever designed this puzzle: well done! It was very interesting.